By Tom Barton, Internet2 Research Engagement
Estimated reading time: 3 minutes
In the Fall of 2020, the National Institutes of Health (NIH) announced that they were making changes to increase the security of many of their services to better protect the sensitive data shared with researchers. Among those are requirements for federated logins:
- Release Necessary User Information – Release the user information defined in the REFEDS Research & Scholarship (R&S) entity category.
- Multi-factor Authentication – Implement multi-factor authentication (MFA) request and response signaling using the REFEDS MFA Profile and perform MFA for a user when requested.
- Share identity assurance information – Signal user identity assurance information using the REFEDS Assurance Framework.
Their approach, being implemented in partnership with InCommon, is to gradually enforce these requirements over time and across specific NIH services, matching each requirement to the needs of each service rather than requiring all of these measures for all of their services.
NIH created a tool that administrators of Identity Providers can use to check whether they are configured to meet each of these requirements.
Releasing R&S user information to NIH not only meets one of these requirements, but it also enables the automatic enrollment of Identity Providers that support the R&S entity category into NIH’s federated login service. The InCommon community has responded with a substantial increase in R&S participation by Identity Providers, as shown here.
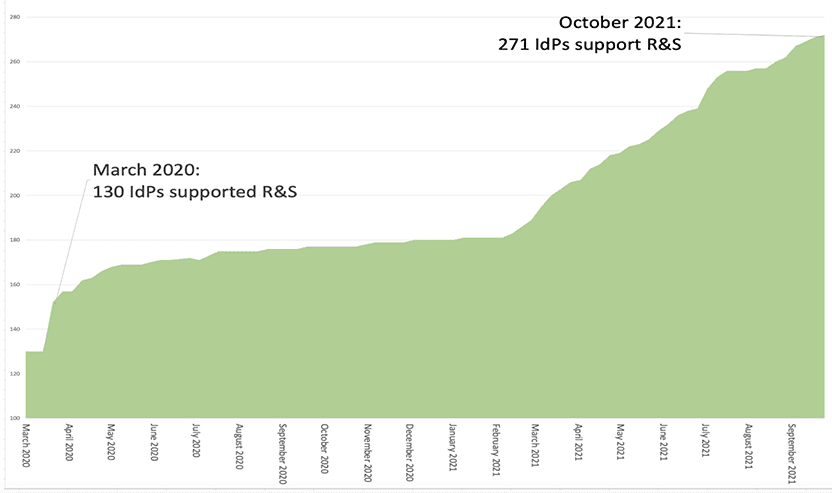
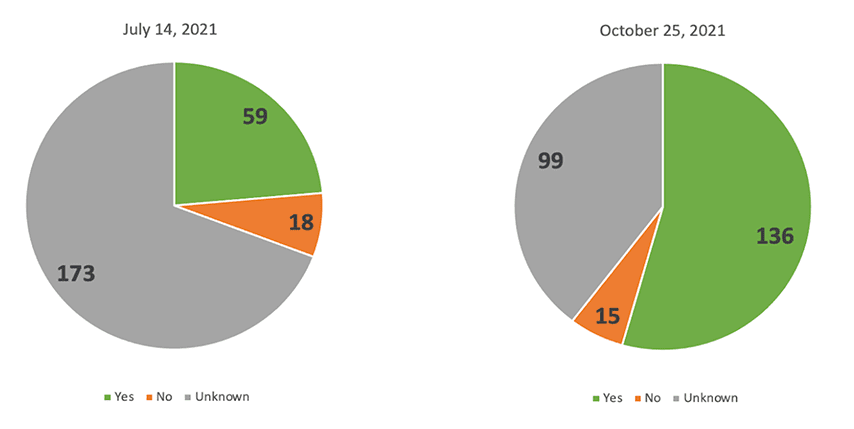
The first NIH service to implement the MFA requirement was the electronic Research Administration (eRA), which went live with MFA on September 15, 2021. The following graphic shows the increased implementation of MFA by InCommon Identity Provider organizations that receive NIH funding.
NIH is still determining which of its services will require specific identity assurance levels, of which there are several in the REFEDS Assurance Framework: low, medium, high, and local enterprise. The general approach will be to start with local enterprise, which is comparatively easy for InCommon Identity Providers to meet, and move over time to medium or high for NIH services that need that level of identity assurance. Current planning dates for the initial requirement of these are as follows:
| Identity Assurance level | Planned initial requirement date |
| local enterprise | June 30, 2022 |
| medium and high | December 31, 2022 |
Detailed guidance for InCommon Identity Providers on how to meet each of these identity assurance levels was created by members of the InCommon community collaborating in InCommon’s Assured Access Working Group. This guidance, as well as additional information to help with the implementation of all of the NIH security measures for federated access, can be found on the Get NIH Ready wiki page.
Stay tuned as InCommon will be hosting additional virtual Office Hours to answer your questions and help Identity Providers navigate how best to support NIH’s security measures.
