By Tom Barton, InCommon Research Consultant, Internet2
In Fall of 2020, leaders from the National Institutes of Health (NIH) first addressed the InCommon community about how allowing researchers to use InCommon-enabled home credentials made it easier and faster for them to collaborate on the development of the COVID-19 vaccine.
At Internet2’s TechEX 2020, they highlighted three aspects of federated logins that help the agency manage risk:
| InCommon/NIH Community Update: MFA and Identity Requirements Webinar |
| Join us on Thursday, April 20 at 2 p.m. ET for a briefing on the InCommon Community’s readiness to support NIH. Register now. |
- User Attributes from the Research & Scholarship Entity Category, which enable automatic enrollment of Identity Providers that support the R&S Entity Category into NIH’s federated login service and smooths the user experience.
- Multi-Factor Authentication (MFA), signaled by the use of the REFEDS MFA Profile, a security measure now required to access most NIH services.
- Identity Assurance Information, conveyed using the REFEDS Assurance Framework, (RAF) another security measure becoming required by NIH services that provide access to sensitive data as those services adapt to meet recent federal security requirements.
Since then, NIH has provided tools and data and coordinated with Internet2 on outreach efforts aimed to help InCommon participants concerned with supporting their NIH researchers to enhance their identity and access management (IAM) processes and technology to enable these aspects of federated logins.
Our Progress Thus Far
So how’s it been going? There’s good news and bad news.
First, the good news:
- Automatic enrollment of campus Identity Providers, which enable researchers and research administrators to use their campus credentials through InCommon, has reduced previous cycle times from several weeks down to one day.
- In addition, support of MFA signaling by campus InCommon Identity Providers (IdP) increased by over 200%. The following graph shows how InCommon members responded strongly to the announcement by the electronic Research Administration (eRA), the NIH grants management system, of a September 2021 deadline for MFA.
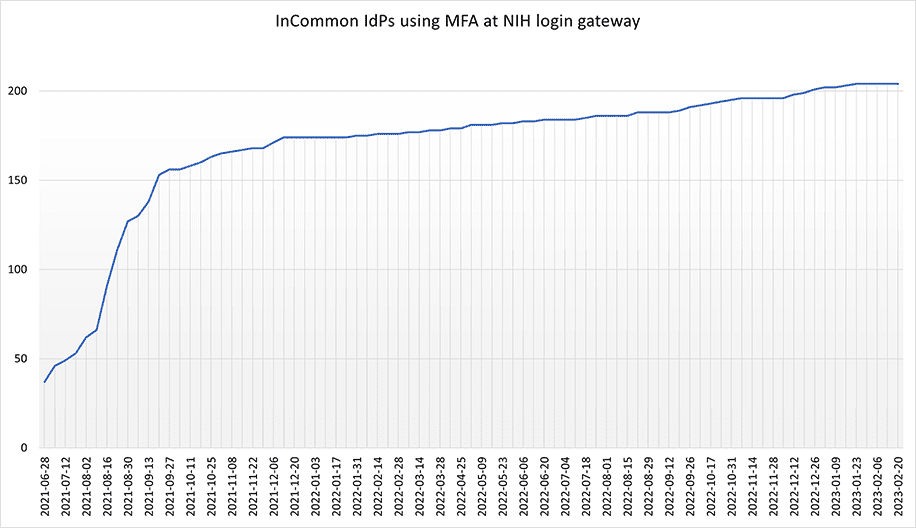
What’s the not-so-good news?
Across those 200+ schools, many campus researchers involved with NIH projects have chosen to use login.gov credentials over their campus credentials.
The following graph, based on login data gathered at the NIH Login Gateway, shows how often researchers at the top 40 research and education organizations, in terms of overall NIH grant funding, chose to use their campus credentials versus login.gov credentials to access eRA.
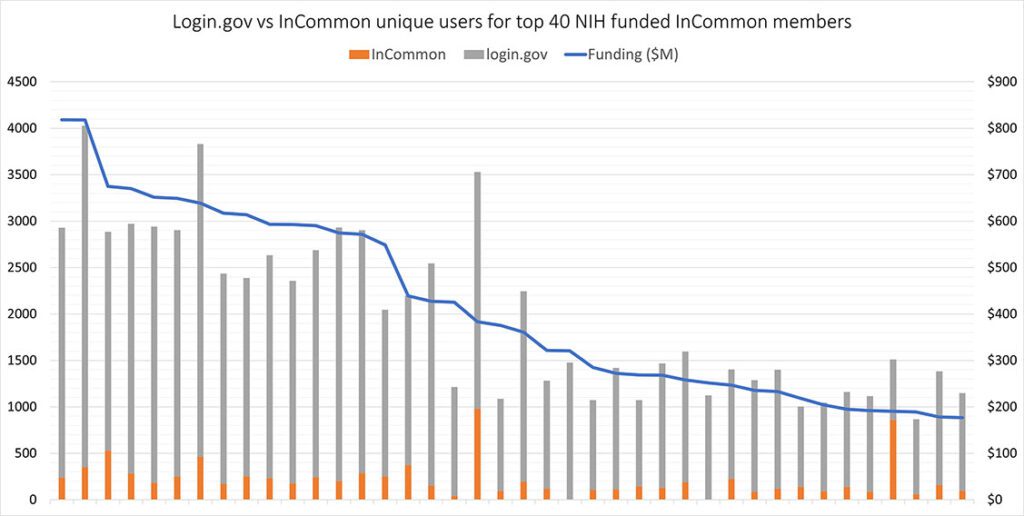
So why haven’t campuses taken full advantage of the investment they made to ease their researchers’ access to eRA and NIH data services? One theory is that researchers are unaware that they can use their campus credentials.
If your college or university is InCommon-enabled for NIH access, consider reminding your research community that they can use their campus credentials to access NIH resources through InCommon. You’ve already done the work! It’s time to get a return on your investment!
Where to Next? Get Ready for Identity Assurance Requirements
Given the sensitive nature of NIH data services, researchers will need to be adequately identity-proofed either to NIST standards or to the roughly equivalent global research and education federation standard, the REFEDS Assurance Framework. Identity proofing is checking that someone is who they claim to be, usually by comparison with government-issued identification like driver’s licenses or passports, similar to what institutions do when hiring employees. MFA and identity proofing together mitigate the risk that an unauthorized person is given access to sensitive data, as so much of NIH’s data is.
Although specific deadlines have not been determined, it is prudent to begin your implementation of an identity-proofing process sufficient to cover researchers for their work with NIH data services. Consult the InCommon-community report REFEDS Assurance Framework Implementation Guidance for InCommon Participants for practical guidance suited to U.S. colleges and universities. Commercial identity proofing services also exist that you can integrate within your IAM processes. See the Kantara Initiative’s Trust Status List of Component Services for the latest information on which ones are approved.
So, please continue supporting NIH’s requirements for MFA and identity proofing by implementing the standards referenced above, and consider how you can ensure that word gets out to affected researchers at your institution. It really makes a difference.
